WinAC.NET
Access Control
What it Does
WinAC.NET is a powerful, secure and highly scalable software platform integral to Tensor's proven range of Windows-based Access Control products — from simple door and registration point control, through to a fully computerised global Networked Access Control System.
With WinAC.NET and Tensor's range of readers, you can control most standard types of internal and external electronic, magnetic door releases and devices, making full use of location points, whether in full view or hidden out of sight, providing access even in the most adverse conditions.
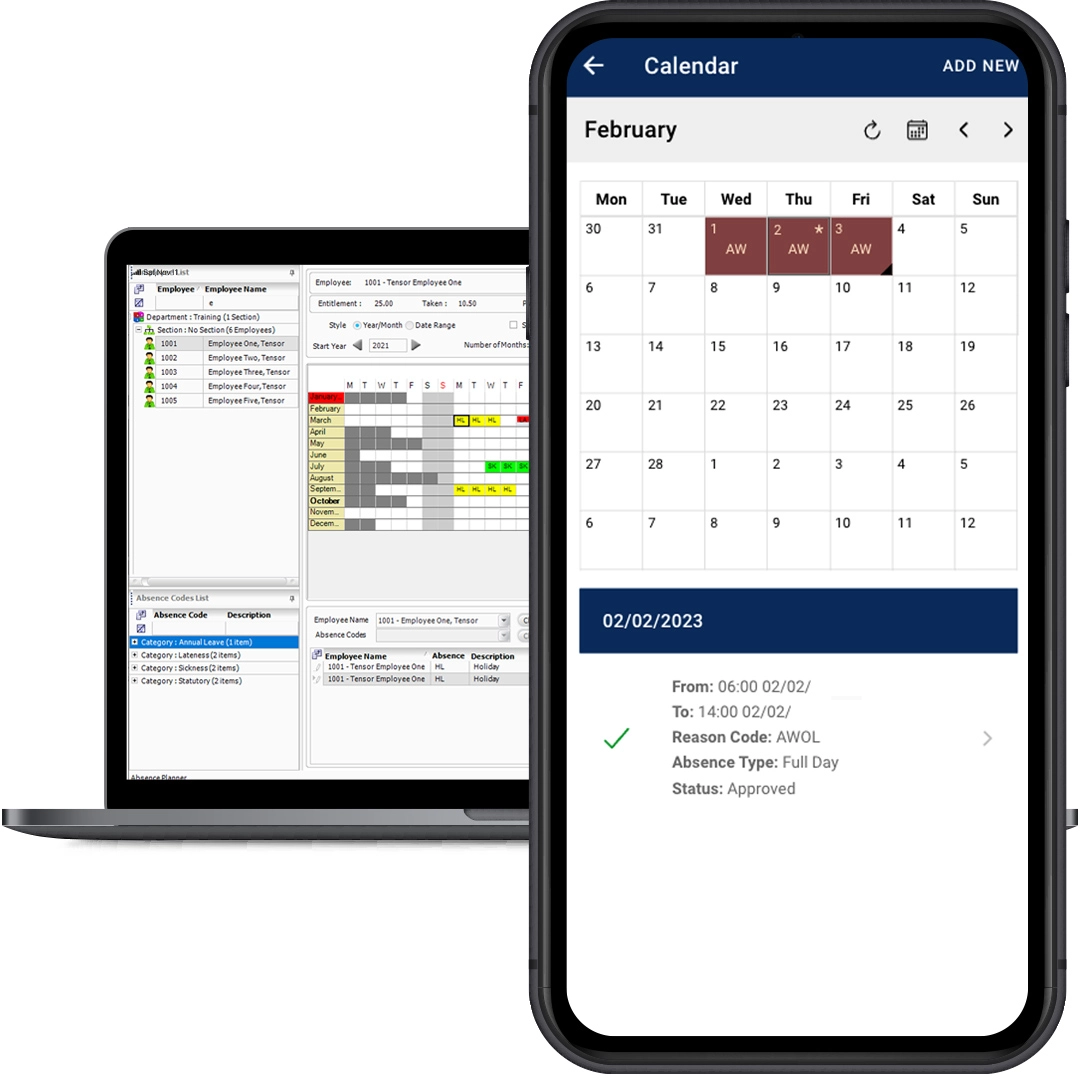
Controlling access within business premises has never been easier.
WinAC.Net is a highly secure way of controlling access to areas or buildings

Ensuring continuous operation
WinAC.NET is a resilient system that keeps running even when certain cables are cut or damaged or PC networks fail.
Frequently Asked Questions
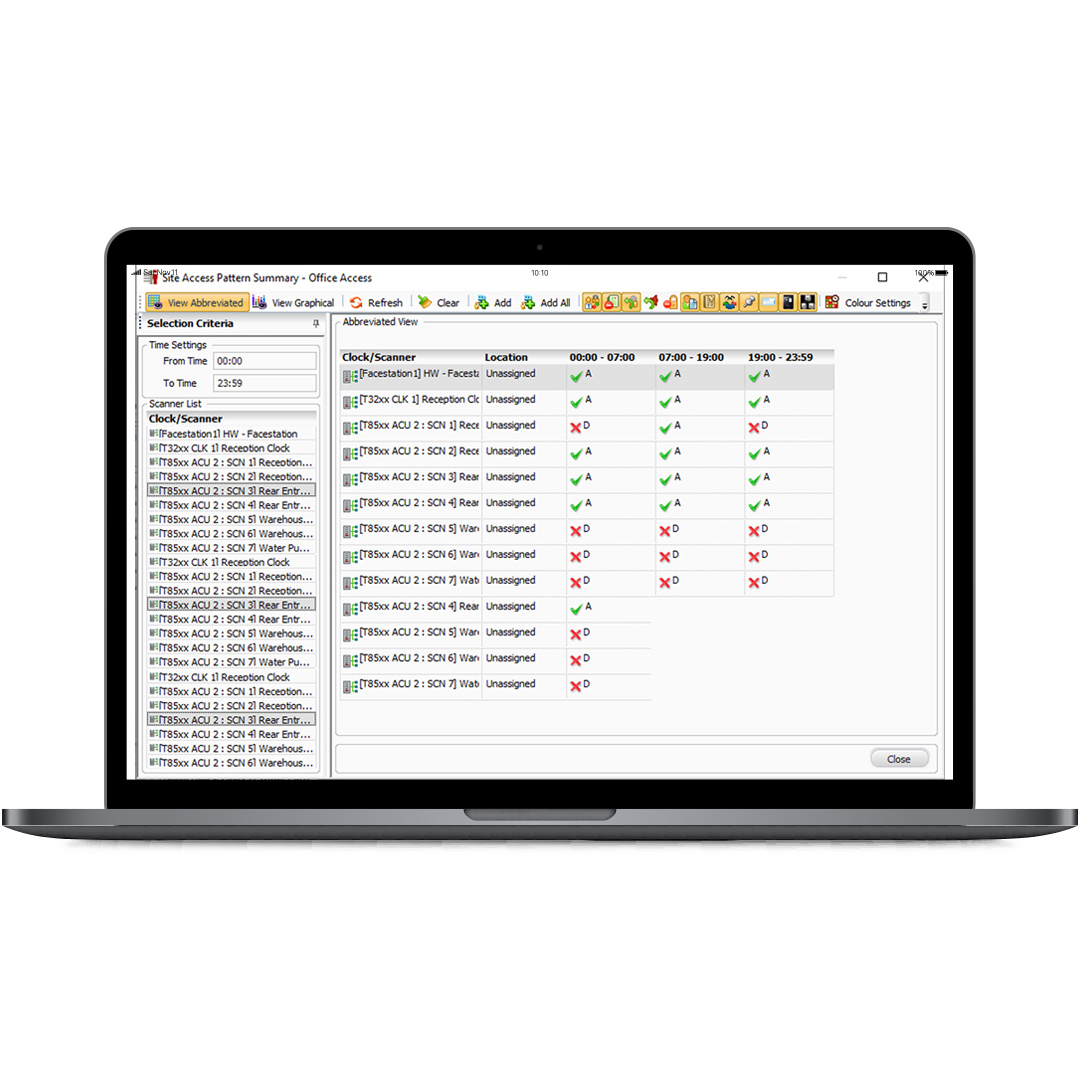
An extensive range of equipment, devices and releases can be connected to your security network, which can be operated through your access control software including:
- Alarms and hooters
- Break glass buttons
- Door locks
- Door release buttons
- Electro-magnetic door locks
- Fingerprint readers
- CCTV cameras
- Scanners

PERFORMANCE AND TECHNICAL SPECIFICATIONS
| Function | Enterprise | Business | Lite | Start |
|---|---|---|---|---|
| Sections — the ability to create sub groups, usually within departments | | | | |
| Pay intervals — employees can be categorised by their payment period interval | | | | |
| Misc groups — categorise employees by two further customisable groupings | | | | |
| Bulk amend — a menu option to change employee details en masse | | | | |
| Active directory — the ability to populate the system's employee list from the users held in your active directory | | | ||
| Global access groups — create access control rules that apply to multiple sites | | | | |
| Calendar groups — this feature allows the days that are treated as public holidays to be varied across a range of employees | | | | |
| Fire Roll Call points — the ability to create fire assembly points for fire roll call reporting | | | | |
| Auditing — includes functionality to record and report upon user system activity | | | | |
| Security groups — can be used to restrict the employees visible to system users | | | | |
| Role management — can be used to restrict the functions visible to system users | | | | |
| Company group | | | ||
| Locations | | | |